HTTPS protocol: what it is, how it works, what SEO advantages it gives
If a website doesn’t protect user data, why should visitors trust it? This is the question that browsers and search engines ask themselves every day, and the answer is HTTPS: once reserved for banking portals and e-commerce, today it is considered the minimum standard for any website, from large companies to small blogs, and in fact today almost 88% of all websites in the world use this protocol. HTTPS is the basic requirement for ensuring a reliable, web because every time we surf the web we share information that can be intercepted, altered or stolen, and it is unthinkable to leave a site without an encrypted connection, even for mere practical reasons. The main browsers clearly mark pages without HTTPS as “not secure”, discouraging users from continuing to browse them, and Google intervenes in an equally drastic way, using the adoption of an SSL certificate as a (weak) ranking factor. So let’s focus on the HTTPS protocol, how it works, the advantages it offers from a technical and SEO point of view and how to implement it smoothly, thanks also to Google’s advice and best practices.
What is HTTPS
HTTPS is the protocol that guarantees the security of data transmission on the Internet, preventing information from being intercepted or modified during its transfer between a browser and a website. Based on TLS encryption (formerly SSL), it creates a secure channel that ensures confidentiality, integrity and authentication in online communication.
Thanks to its innovative characteristics compared to the previous HTTP protocol, it has become a standard to guarantee greater security and privacy for users, especially when entering sensitive information such as login credentials and bank details. More specifically, HTTPS is the direct evolution of HTTP, to which it adds an encryption layer based on the TLS (Transport Layer Security) protocol, designed to prevent interceptions, tampering and cyber attacks along the data path and to guarantee that the transmitted data is encrypted and therefore inaccessible to third parties.
Today it is an essential – and minimum – standard for the modern web, to the point that search engines favor pages that use it and browsers explicitly report sites that don’t have it. Any platform – from online stores to personal blogs – should adopt it to guarantee reliable navigation for its users and protect both its image and the sensitive information transmitted over the network. However, HTTPS is not an option that only concerns cybersecurity: its impact extends to SEO, site performance and user experience, because in addition to protecting content during data exchange, it helps create a more transparent, reliable and efficient digital environment.
What does the acronym HTTPS mean and what does it represent?
HTTPS stands for HyperText Transfer Protocol Secure. It is the method by which browsers and servers communicate with each other, guaranteeing that the information transmitted cannot be read or altered by external parties, thus protecting the integrity and confidentiality of the data between the user’s computer and the website.
The main difference compared to HTTP (HyperText Transfer Protocol) is the additional security level based on TLS (formerly known as SSL, Secure Sockets Layer) encryption. While HTTP transmits data in clear text, making it vulnerable to interception or modification, HTTPS encrypts the information flow and prevents third parties from accessing the transmitted content.
This feature is also reflected in the user experience. In some modern browsers, HTTPS sites are marked with a padlock next to the URL, a visual indicator that immediately communicates the presence of a secure connection. Conversely, the absence of the protocol leads to explicit “unsafe site” warnings, a deterrent that can drastically reduce trust in a page and affect user interactions.
Google’s definition of HTTPS
As John Mueller, Google’s Search Relations Lead explained in one of the Search Central Lightning Talk series events on YouTube, the definition of HTTPS is “a protocol that identifies a secure connection between a site and its users, protecting the site from unwanted activity”.
In terms of security, HTTPS ensures three things in particular:
- Authentication. The SSL (Secure Sockets Layer) or TLS (Transport Layer Security) certificate used in the https protocol allows the identity of the site to be verified, in turn guaranteeing that users are connected to a legitimate site. This is a way of giving users the certainty that they are interacting with the desired website and not an intermediary.
- Data integrity. The encryption used in the protocol establishes a secure connection, which prevents the modification and tampering of transmitted data, guaranteeing the integrity of the information exchanged between users and the website and allowing users to see the content as expected.
- Encryption. The information exchanged between the client and the server is encrypted, and this guarantees that the information exchanged between a website and its users will be kept safe and secure, and that the data communication will be protected from interception by third parties.
These are three fundamental pillars for a modern, secure and reliable web, because “your users should feel safe on your site, just like they feel when they visit your company in person”.
Is HTTPS really synonymous with security?
Let’s clarify one aspect right away: associating HTTPS with security is correct, but only in reference to the protection of data transmission between the browser and the server. This technology prevents the interception of communications, but in itself does not guarantee that the website is reliable or free from threats.
A malicious site can still obtain an HTTPS certificate and appear visually secure to users. This is the case with many phishing pages designed to deceive visitors and extort sensitive information. The simple padlock next to the URL is not an absolute guarantee (and in fact the FBI has often warned about this issue), because it only indicates that the connection is encrypted, without expressing any judgment on the legitimacy of the content or the integrity of the site administrator.
In short: HTTPS is an essential element for online security, but it must be accompanied by other protective measures. In addition to correctly configuring certificates and managing technical updates, users must always verify the authenticity of a domain, and avoid entering credentials or sensitive data on suspicious pages. Therefore, regardless of the padlocks and browser indications, it’s always best to keep your eyes open when it comes to entering sensitive data on the web.
How HTTPS works technically
The main function of HTTPS is to protect the data that travels between a user and a website’s server, using an encryption system that prevents unauthorized access or alteration of information during transfer. This protection is achieved through three key elements: the TLS protocol, the asymmetric key encryption system with public and private keys, and the TLS Handshake process, a negotiation mechanism that establishes a secure connection before starting the information transfer.
The protocol doesn’t just encrypt the data, but ensures the identity of the website and protects its integrity, preventing it from being intercepted, manipulated or read by malicious individuals. This protection is particularly important in a context where more and more sensitive information is transferred online, from access credentials to financial data. However, we reiterate, the simple use of HTTPS does not completely eliminate security risks: although it makes information encrypted, it does not prevent phishing attacks or problems related to untrustworthy certificates.
The role of the TLS/SSL protocol
The HTTPS protection mechanism is based on the TLS protocol, which has replaced the historic SSL standard. Although the term “SSL” is still commonly used, it is now obsolete and vulnerable to various security flaws.
The evolution from SSL to TLS was driven by the need to improve security and performance. TLS uses more modern encryption algorithms and more robust authentication mechanisms, which have made it possible to overcome some vulnerabilities that exposed SSL to interception and man-in-the-middle attacks. Today, the most popular browsers exclusively support TLS 1.2 and TLS 1.3, while previous versions have been deprecated for security reasons.
Specifically, the protocol uses an advanced encryption system to guarantee the secure transmission of information, eliminating the possibility that it could be read or altered by third parties. It therefore doesn’t just protect browsing, but also allows the identity of the website visited to be authenticated, helping to reduce the possibility of users falling victim to fraudulent sites.
Encryption and public/private keys
HTTPS is based on a system of encryption with an asymmetric key, a method that uses two different but closely related cryptographic keys to create a secure connection between the client and the server.
The public key is accessible to anyone and is used to encrypt data before sending it to the server. The private key, on the other hand, is kept by the server and is used to decipher the information received. This architecture guarantees that only the authorized recipient can read the transmitted information: even if a malicious person intercepted the data flow, they would have no way of reading it without having the corresponding private key.
Once the initial connection has been established, the protocol switches to a symmetric encryption system, which is faster and less computationally demanding. This mechanism maintains high security standards without compromising transmission speed and site performance, guaranteeing a smooth and protected browsing experience for users.
The TLS Handshake process
Before data can be transmitted securely, the browser and the server must agree on a secure communication channel: this is done through the TLS Handshake, a sequence of exchanges that allows the two parties to establish an encrypted connection and verify the authenticity of the website.
In this phase, the browser sends a request indicating the supported TLS versions and compatible cryptographic algorithms. The server responds by choosing the most advanced security settings available, sending its digital certificate to the browser, which contains the public key for encryption. The browser verifies that the certificate has been issued by a recognized authority and, if the outcome is positive, starts exchanging the session key, which will be used to encrypt subsequent communications.
In summary, the TLS Handshake is divided into these steps:
- Client Hello: the browser sends a request to the server, including the supported TLS versions and compatible cryptographic algorithms.
- Server Hello: the server responds, choosing the most secure TLS version and sending its digital certificate.
- Verification of the certificate: the browser checks the authenticity of the certificate, verifying that it has been issued by a reliable certification authority.
- Exchange of the session key: a shared key is generated, used to encrypt the subsequent communication.
- Secure session activated: the encrypted channel is stable and the data transmission can take place in a protected way.
The entire “handshake” process takes place in a few moments and has a minimal impact on the site’s performance, but it is essential to ensure that the connection is truly secure and that the data exchanged between the user and the server is not accessible to anyone else.
What is the HTTPS certificate and what is it for?
The element that makes it possible to identify a site as secure is the digital certificate, an electronic document issued by a certification authority (CA). This certificate serves to guarantee the identity of the website owner and to confirm that the connection is effectively protected.
There are different levels of certification, based on the quantity and type of checks carried out on the legitimacy of the entity requesting the certificate; the three best known and most widespread are:
- Domain Validation (DV): only verifies that the site owner controls the domain, without any other guarantees regarding the identity of the organization.
- Organization Validation (OV): includes additional checks to verify the existence of the company or organization that requested the certificate.
- Extended Validation (EV): provides the highest level of verification, certifying specific company details and displaying the organization’s name in the browser address bar.
Using a valid certificate is essential to avoid security warnings in your browser, improve user trust and optimize your position in search engines.
HTTPS vulnerabilities: what it doesn’t protect
We’ve already said it: HTTPS is a fundamental step in browsing security, but it is not an all-powerful solution against all cyber threats. It only protects the transmission of data, without offering any guarantees about the nature of the site or the content it displays. A fraudulent domain can still obtain an HTTPS certificate and appear secure to the user, tricking them into entering confidential information into deceptive forms – this is a typical case of phishing.
Another critical issue concerns domain name resolution, also known as DNS leaks: the encryption of HTTPS only protects the traffic between browser and server, but does not prevent the tracking of DNS requests. Therefore, even if the traffic between the browser and the server is encrypted with HTTPS, the DNS requests necessary to reach the site can reveal information about the navigation to providers, government agencies or other network intermediaries. Integration with new technologies such as DNS-over-HTTPS (DoH) aims to mitigate this problem, although it is not yet a universally adopted solution.
Finally, there are cyber attacks that can circumvent some of the benefits of HTTPS. A cybercriminal could force a downgrade of the security protocol, forcing the connection to use obsolete and vulnerable versions. Even the use of self-signed certificates, not verified by a public authority, can render the protection offered by the protocol ineffective, deceiving users with sites that only appear to be reliable.
To ensure a truly secure digital environment, the HTTPS protocol must be supported by other protective measures. Continuous monitoring of the site configuration, timely reporting of expired or compromised certificates, and educating users on how to recognize phishing attempts are essential aspects of an effective cybersecurity strategy.
HTTPS and HTTP: the main differences between the protocols
HTTP and HTTPS are both protocols used for the transmission of data between a website and a user’s browser. Their basic structure is similar, but the main difference lies in the level of data protection offered by HTTPS thanks to the integration of the TLS protocol. This completely changes the way information is managed in transit, making HTTPS the only choice for anyone who wants to guarantee a secure connection: in short, HTTPS has already emerged as a more secure and effective version of the previous generation of protocols for transmitting data between a browser and a server via the web, namely HTTP, adding a layer of security through SSL/TLS encryption.
While HTTP transmits data in clear text, allowing it to be read or altered by unauthorized third parties, HTTPS uses encryption to prevent its manipulation. HTTP was basically designed for the rapid transmission of information via the web, and the absence of encryption made it simple to implement and light on computational resources, but exposed it to significant vulnerabilities, such as the risk of interception and alteration of the transmitted content.
HTTPS introduces encryption of data using TLS, ensuring that information remains confidential during transfer: the encryption process involves a slight increase in the load on servers, but this disadvantage is more than compensated for by the improvements in terms of protection, performance and reliability.
This distinction is also reflected in practice: HTTP sites are flagged by browsers as “not secure”, while HTTPS is now the standard required by Google and the major search engines to ensure a more reliable web.
Another important distinction concerns browser support. HTTPS is now the default configuration accepted by Chrome, Firefox, Edge and Safari, while HTTP sites are indeed flagged as insecure, discouraging users from visiting them.
Furthermore, HTTPS provides an authentication mechanism thanks to the use of SSL/TLS certificates, which allow users to verify the identity of the website they are accessing, thus guaranteeing that it is a legitimate site and not a fraudulent copy. On the contrary, HTTP does not have such an authentication system, making it difficult for users to understand if a website is genuine or fictitious.
Another important aspect of the differences between HTTP and HTTPS concerns data integrity: with HTTP, the transmitted data could be altered by malicious external agents during transit between the client and the server. This risk is substantially eliminated with HTTPS, as encryption prevents data from being modified, guaranteeing that the information exchanged is not compromised.
Implementing HTTPS isn’t just about security, it also affects the speed and performance of a website. The HTTP/2 and HTTP/3 protocols, which improve the efficiency of page loading, are only compatible with HTTPS connections. Adopting this standard is therefore a requirement not only to protect data, but also to ensure smoother and more efficient browsing.
Port 80 vs. Port 443: why the difference is important
Web traffic is based on specific communication ports, which determine the type of protocol used for the exchange of information between browser and server. HTTP works through port 80, while HTTPS uses port 443, which offers an additional layer of security thanks to TLS encryption.
This technical difference has direct implications on the connections established by browsers. When a user types a web address without explicitly specifying the protocol, the browser automatically selects the default port. If the site is not properly configured to force HTTPS, access could be via HTTP without any protection of data transmission.
Using only port 443 ensures that all communications between the browser and the server are encrypted, reducing the risks associated with man-in-the-middle attacks and content manipulation. On a practical level, many modern configurations provide for an automatic redirection of HTTP requests to HTTPS, forcing the use of a secure connection to protect users and improve the ranking of the site on search engines.
HTTPS as a requirement for HTTP/2 and HTTP/3
The new versions of the HTTP protocol are designed to improve the efficiency of data transmission, reducing latency and optimizing the loading of web pages. However, a fundamental prerequisite for benefitting from these innovations is the adoption of HTTPS.
HTTP/2 introduces significant improvements over the previous version, including multiplexing requests, which allows the browser to download multiple resources simultaneously from the same server, reducing page loading times. HTTP/3, on the other hand, is based on the QUIC protocol, which uses a different architecture to make the connection faster and more resilient to network errors. Both protocols are only available over HTTPS, as mentioned, making the implementation of a secure connection a necessary step for those who want to improve the performance of their site.
The history and evolution of protocols: from SSL to HTTPS
The evolution of HTTPS is closely linked to advances in computer security and the need to protect online communications, which has led to decades of innovation, standardization and awareness of data protection. From the first HTTP protocol, lacking any security measures, to the widespread adoption of HTTPS and modern cryptographic updates, the history of a universally adopted protocol for Internet communications has its roots in the late 1980s and is divided into these most relevant events.
- 1989-1991: the introduction of HTTP and the first web transmissions
The HTTP (Hypertext Transfer Protocol) was introduced in 1989 by Tim Berners-Lee, the creator of the World Wide Web, at CERN, the European Organization for Nuclear Research. HTTP was created as a basic mechanism for the transmission of hypertext documents, allowing browsers to request and receive content from a web server, and together with HTML (Hypertext Markup Language) was part of the WWW project, which aimed to create a system of interconnected documents accessible via the Internet.
In 1991 the first version of the protocol, HTTP/0.9, was formalized, with functionality limited to simply requesting and sending HTML documents. However, the absence of security mechanisms made the information visible to anyone who intercepted the network traffic, a problem that became more evident with the increase in Internet use. In practice, any communication, including confidential information such as credentials and credit card numbers, could be intercepted by malicious actors through techniques such as the man-in-the-middle (MitM) attack. As the use of the web expanded rapidly, especially for commercial and financial purposes, it became necessary to develop a system to protect transmissions.
- 1994-1996: SSL arrives
The first attempt to protect data transmission was made in 1994 by Netscape Communications Corporation, led by Taher Elgamal, who developed the SSL (Secure Sockets Layer) protocol. This technology was designed to encrypt communications between browsers and servers, offering an additional level of security, essential for sites that handled sensitive information.
- SSL 1.0 was never released due to serious security flaws.
- SSL 2.0 was introduced in 1995 with support for public key cryptography and the generation of encrypted session keys, improving data protection.
- SSL 3.0, released in 1996, further refined the protocol, introducing more robust encryption mechanisms and better authentication systems. Over time, however, even this version proved vulnerable to exploits such as BEAST (Browser Exploit Against SSL/TLS).
Despite the advances, SSL remained vulnerable to various attacks, and the need for more solid protection led to the birth of the next security standard. However, the infrastructure of SSL 3.0 was later adopted as the basis for the creation of the TLS protocol.
Also in 1996, the standard HTTP/1.0 (RFC 1945) was published, introducing new features and improvements over the previous version.
- 1996-1999: the evolution from SSL to TLS
In 1999, the Internet Engineering Task Force (IETF) developed TLS (Transport Layer Security), an update designed to eliminate the security flaws of SSL. TLS 1.0 incorporated more advanced encryption, data integrity protection and improvements in the handshake between browser and server.
At the same time, HTTP 1.1 (released in 1997 as RFC 2068) became the new standard for managing web communications, introducing improvements in the management of persistent connections. However, HTTP 1.1 did not directly integrate security, making it necessary to associate it with TLS to obtain encrypted connections.
- 2000: the official birth of HTTPS
In 2000, with the combination of HTTP and TLS, HTTPS (Hypertext Transfer Protocol Secure) was officially born. With this configuration, websites could guarantee authentication, encryption and data integrity, almost completely preventing the interception of information.
However, in the early 2000s HTTPS was mainly adopted by banking sites, e-commerce sites and platforms that managed sensitive information. Standard websites, without critical data, continued to operate without any protection, mainly due to the cost and complexity of implementation. More precisely, according to the experts, among the reasons for the lack of global diffusion of HTTPS there have historically been issues of a technical, economic and practical nature: adopting the SSL certificate had a cost that was excessive for many sites, especially for small projects that perhaps did not deal with sensitive user data; often, then, HTTPS did not work with the cheapest virtual hosts and caused the loss of the ability to cache data.
- 2006-2018: the continuous evolution of TLS and the widespread adoption of HTTPS
Although TLS 1.0 offered greater security than SSL, the evolution of cyber attacks required a constant updating of the protocol:
- TLS 1.1 (2006) improved protection against security key vulnerabilities.
- TLS 1.2 (2008) introduced new, more secure encryption algorithms and a more robust key management process.
- TLS 1.3 (2018) eliminated the old, less secure algorithms, reducing connection times and improving cryptographic protection.
At the same time, the use of HTTPS became more widespread thanks to lower certification costs and the first initiatives to make it the default standard for all websites.
- 2014-2017: Google’s push for HTTPS Everywhere
A decisive moment came in 2014, when Google announced that HTTPS would be a ranking factor in search results. This incentive prompted many website owners to consider implementing the secure protocol to gain a competitive advantage in SEO. In addition, starting in 2017, the major browsers began to apply stricter measures against HTTP sites.
Google Chrome, in particular, introduced security warnings visible to users: any site without HTTPS was flagged as “Not secure”. Mozilla Firefox, Microsoft Edge and Safari also aligned themselves with this policy, directly influencing users’ choices and contributing to the transformation of HTTPS into a mandatory standard for any online project.
Added to this evolution was Let’s Encrypt, launched in 2015 as a free SSL/TLS certification service. Thanks to Let’s Encrypt and a growing awareness of online security, obtaining and renewing an HTTPS certificate became more accessible and automatic.
In recent years, we have also seen:
- The integration of HTTPS by default on many platforms such as WordPress, Shopify and cloud hosting services.
- The spread of free solutions beyond Let’s Encrypt, making the implementation of HTTPS easier and more accessible.
- The official entry of HTTPS into the Google Page Experience framework, confirming its impact on SEO.
- Today: HTTPS as a universal standard
Currently, about 90% of websites use HTTPS and browsers no longer support insecure protocols such as TLS 1.0 and TLS 1.1. HTTP is no longer an acceptable solution, not only from a security point of view, but also in terms of user experience and SEO.
The evolution of HTTPS has not stopped: the protocol continues to adapt to new cyber threats and integrates with the latest web technologies, in particular with the use of HTTP/2 and HTTP/3.
The advantages of HTTPS for websites
The path just described should have further clarified why adopting HTTPS today is no longer an optional choice, but an indispensable requirement for anyone who wants to guarantee a reliable browsing experience. In addition to protecting the exchange of sensitive information, this protocol is a fundamental requirement for accessing modern technologies, improving the performance of web pages and consolidating user trust.
Its impact is not limited to e-commerce sites or platforms that manage confidential data. HTTPS has become a mandatory standard for any online project, from personal blogs to company portals, as it affects not only security but also visibility in search engines and compatibility with the most advanced web tools.
The adoption of HTTPS is now necessary for:
- E-commerce sites and online payments, where transaction security is a priority.
- Platforms that collect personal data or login credentials, such as home banking portals, social media and login forms.
- Sites that want to be visible on Google, both because HTTPS is a ranking signal recognized by the search engine, and (especially) because all competitors use it.
- Websites that use modern technologies, such as HTTP/2, Progressive Web Apps (PWA), geolocation and push notifications.
It is no longer just a question of protection, but of remaining competitive on a web that is increasingly demanding in terms of security and performance.
Protecting sensitive data and preventing attacks
As mentioned, HTTPS was developed to prevent data transmitted between a user and a server from being intercepted or modified by third parties. This protection is essential when dealing with sensitive information such as passwords, credit card numbers and authentication details.
The protocol works by encrypting the data with TLS before it is sent over the network, preventing it from being read in case of interception. This blocks man-in-the-middle attacks, one of the most common threats to HTTP connections, in which an attacker intercepts and alters the communication between the browser and the website.
Another crucial advantage is data integrity. With HTTP, the information exchanged between the client and the server can be manipulated and tampered with before reaching the end user, making it possible for cybercriminals to spread malware or modify content. HTTPS guarantees that pages are loaded exactly as they were sent by the server, without the risk of external tampering.
Improved user confidence and experience
Web pages served via HTTPS display a padlock next to the URL in modern browsers, an immediately recognizable signal for users. This simple icon has a significant impact on the perceived security of the site and can influence the decision to continue browsing or leave the page.
Several studies have shown that not using HTTPS can reduce the conversion rate. When a site is flagged as “not secure”, users are more inclined to reconsider entering personal or payment details. In the case of e-commerce, for example, this perception translates into an increase in the abandoned cart rate.
Adopting the secure protocol not only prevents these problems, but also helps strengthen the reputation online of the company or professional using it. A site with HTTPS inspires greater reliability and demonstrates attention to user security, an element that, in the long term, can promote loyalty and improve the overall user experience.
Influence on performance and loading times
One of the lesser-known aspects of HTTPS is the contribution it offers in terms of speed. Although encryption requires a slight increase in computational load, this difference is more than compensated for by the optimizations introduced with HTTP/2 and HTTP/3, protocols available only for HTTPS connections.
With HTTP/2, resource loading becomes significantly more efficient thanks to multiplexing, which allows downloading multiple elements simultaneously without unnecessary delays. While with HTTP each request was handled individually, causing slowdowns, with HTTP/2 the browser can receive multiple data in parallel, reducing overall loading times.
HTTP/3 brings further improvements thanks to the adoption of the QUIC protocol, which eliminates some of the limitations of traditional TCP-based protocols, improving connection responsiveness and reducing latency. For those who manage sites with intensive data flows, such as streaming platforms or interactive content services, the advantages in terms of performance are evident.
Compatibility with modern browsers and advanced features
HTTPS is not just a security measure, but a technical requirement for many of the advanced features demanded by the modern web. Browsers such as Chrome, Firefox and Safari have introduced progressive restrictions on non-HTTPS sites, limiting access to certain technologies that can improve the user experience.
Today, only sites that use HTTPS can take advantage of essential tools such as:
- Geolocation, used by e-commerce and location-based services.
- Push notifications, functional for marketing and user loyalty.
- Progressive Web Apps (PWAs), web applications that offer similar functionality to native ones, such as offline support.
Those who manage a site without HTTPS exclude themselves from these opportunities, risking providing a lower browsing experience than their competitors. Furthermore, browsers are progressively blocking key features for HTTP sites, such as access to mobile device sensors or local storage of user data.
HTTPS and SEO: impact on ranking and organic search
Let’s start with the facts.
HTTPS is an element that Google considers when evaluating websites. To be precise, since 2014 HTTPS has been a definite ranking factor for the search engine, which in an official post announced that from that moment on, a website encrypted with HTTPS would get a boost in the rankings compared to HTTP sites.
The real effect of this boost has never been specified, but it was clear from the start that it had limited weight. In practice, HTTPS was a tiebreaker signal, able to make a difference in ranking positions only when two pages were substantially equivalent in terms of quality and authoritativeness. Relevance, in fact, has always been the key to ranking on Google: if a piece of content was the most relevant for a query, it would still rank better even if the site wasn’t HTTPS, while the use of encryption alone was not enough to make poor content quickly climb the SERP. Furthermore, Google preferred to index the HTTPS version if the site had a “mixed” page, served with both an HTTP and an HTTPS address.
Today, as mentioned, it is increasingly rare to find HTTP sites, so the boost has basically disappeared and the protocol is more of a minimum standard. Even if not using the encrypted protocol doesn’t directly penalize a site, it still represents a limitation in the overall evaluation of the site. This is another reason why HTTPS is part of the Page Experience concept, introduced by Google to identify sites that offer an optimal user experience through a series of technical parameters, such as Core Web Vitals and other signals of navigation quality.
However, in addition to the algorithmic aspect, there are more practical implications. In particular, as mentioned, modern browsers flag sites without an HTTPS certificate as “not secure” – and it is not possible to hide whether or not a site uses the system.
In practice, when a user browsing on Chrome lands on a site that uses HTTPS, they don’t see any kind of message: however, by left-clicking on the address bar, the window with the “information” about the site opens, and the first item is the security status. Here they can check if the connection is secure and who verified the certificate.
On the contrary, if we land on a non-HTTPS site the situation changes: the browser bar shows a small “danger” icon on the left, with the words “not secure”. By clicking on it we can read some more information: the browser warns us that the site has not activated a secure connection, inviting us to be careful when sharing any sensitive data.
This impacts the behavior of users, because it could increase the frequency of bouncing and reduce the time spent on pages, factors that can indirectly affect the performance of a site in search results.
Returning quickly to the other possible advantages in terms of visibility, it is estimated that the connection via HTTPS is faster than the connection using the previous protocol, and this can make a difference in terms of performance. Furthermore, returning to the topic of security, HTTPS prevents intermediaries from inserting content into the website without the owner’s knowledge: without HTTPS, a bad actor could inject online ads, for example, to profit from that web traffic (but, again, it does not protect the user’s computer or the web server itself from hacker or malware attacks).
Therefore, even if like any form of security it has weaknesses and may not be infallible, HTTPS is undeniably better than HTTP both in technical terms and from an SEO and user presentation point of view.
Tools to verify HTTPS implementation
Google provides specific tools to monitor the correct implementation of HTTPS. In the Search Console, the dedicated report allows you to check which pages are indexed in HTTPS and to identify any technical problems that prevent the correct transition from the old protocol.
Among the information provided by the report, the main critical issues reported concern:
- Invalid or expired SSL certificates, which prevent the site from being considered secure by browsers.
- Incomplete redirects, which leave some HTTP pages accessible instead of forcing the connection to HTTPS.
- Mixed content, situations in which an HTTPS page loads external resources still in HTTP, compromising overall security.
To ensure an effective migration, it is essential to constantly monitor the status of indexed pages and promptly resolve any reports. An incorrect HTTPS configuration could in fact interfere with the indexing of pages and generate ranking problems.
SEOZoom also has a useful function for more in-depth control over the HTTPS protocol status of your site, Analyze Mixed Content, which is used to identify any errors in the migration or management of the security protocol.
This tool is designed to identify mixed or mixed content, the combinations of a site’s URLs served simultaneously over both HTTP and HTTPS, mainly due to a migration process that has not been perfectly executed or completed. In practice, these are resources such as pages, images, scripts or files that are still being loaded via HTTP even on a site that has now switched to HTTPS. The presence of these elements can not only compromise browsing security, but can also generate warnings in browsers, negatively impacting the user experience. It’s easy to use: just enter the site URL and start the analysis. SEOZoom checks all linked resources, reporting three possible scenarios:
- Everything is ok. If the site is completely in HTTPS, without insecure elements.
- The site does not respond in HTTPS. If the secure protocol is not active and the site still only uses HTTP.
- List of mixed content. If there are resources on the site that have been loaded using both HTTP and HTTPS, the tool displays a detailed list of URLs that are still in HTTP, so you know what to correct to ensure secure browsing.
Analyze Mixed Content is therefore a good ally for those who are updating the protocol of their sites or want to verify if the process has been carried out correctly.
How to activate HTTPS on your website
There are therefore many reasons to adopt HTTPS, and the transition from HTTP to HTTPS is in effect a migration of the site, as HTTPS URLs are different from their HTTP counterparts – and therefore, to perform the transfer, it is necessary to redirect all users with a 301 redirect on the server side for all the URLs on the site.
Implementing HTTPS requires precise configuration to ensure a transition without technical errors or negative impacts on the site’s performance. The process is based on three main phases: obtaining an SSL/TLS certificate, installing and configuring it on the server, and updating all URLs to force the use of the secure connection.
An incorrect migration can cause loss of traffic and indexing problems in search engines. It is essential to perform each step carefully, verifying that all site resources are actually loaded via HTTPS. The major hosting and CMS providers offer guided procedures to activate the certificate, but it is still necessary to check carefully to correct any technical errors and ensure compatibility with the main browsers.
How to obtain an SSL/TLS certificate
Activating HTTPS begins with purchasing or obtaining an SSL/TLS certificate, the essential component that allows for the encryption of communication between the browser and the server. In some cases, the web hosting provider itself provides the certificate (even for free, if included in the current plan), while in other situations it may be necessary to purchase one through the hosting service, a certification authority, a CDN such as Cloudflare or a company such as Digicert, and then install it yourself.
In practical terms, there are free and paid options. Let’s Encrypt, one of the most widely used certification services, offers free, automatically renewable SSL certificates, ideal for blogs, personal websites and small businesses. Companies that require a higher level of verification can opt for certificates issued by authorities such as DigiCert or GlobalSign, which provide additional validation, especially useful for e-commerce and portals that handle sensitive data.
The choice of certificate depends on the needs of the site. A DV (Domain Validation) certificate is sufficient for most projects, while OV (Organization Validation) and EV (Extended Validation) certifications offer higher levels of authentication, clearly indicating the company name in the browser bar.
Furthermore, it may be necessary to periodically renew the SSL/TLS certificates, but above all to check them carefully, because there is the possibility that someone can falsify an SSL/TLS certificate: when this happens, the preventive action of HTTPS against man-in-the-middle (MitM) attacks clearly fails. To avoid trouble and unpleasant situations, therefore, even Google recommends that we examine the certificates issued for the website we don’t recognize and limit the authorities that can issue certificates for a domain using CAA (Certification Authority Authorization) resource records.
It is important to remember that only a valid SSL certificate – and in use on all the pages of the site – allows HTTPS encrypted connections to be established. The absence of encryption or the presence of errors makes all the data sent to and received from the site visible, exposed and therefore potentially manipulable by third parties. To verify the validity of the SSL certificate we can carry out manual tests on the pages, and find out if the browser correctly identifies the padlock, or use specific tools such as those mentioned above.
Installation and configuration of the HTTPS certificate
Once you have obtained the certificate, you need to install it on the web server and configure the settings to ensure that all connections are secure. The procedure varies depending on the technology used to host the site.
On shared hosting platforms, installation is often done automatically via the control panel, with options that allow you to activate SSL in a few clicks. In customized environments, such as Apache or Nginx servers, the certificate must be uploaded manually and activated by modifying the configuration files.
In the most popular CMSs, such as WordPress and Shopify, certificate management is simplified by plugins or dedicated settings that facilitate the transition to HTTPS, ensuring the correct application of the protocol on all pages.
One aspect that is often overlooked is the configuration of the TLS protocol: it is advisable to activate only recent versions (TLS 1.2 and TLS 1.3) to avoid vulnerabilities related to obsolete standards.
Redirecting and updating URLs to HTTPS
Activating HTTPS without correctly implementing redirects can generate access errors and expose the site to problems of duplicate content between HTTP and HTTPS versions. To avoid this scenario, it is necessary to configure 301 redirects on the server side, so as to automatically redirect all HTTP requests to the secure version of the site.
Updating the URL architecture must also include internal links, images and resources such as CSS files and JavaScript scripts. Manually modifying each reference can be complex in larger sites, which is why the use of dedicated scanning tools or plugins can simplify the process.
It is equally important to inform the analysis and marketing services of the new structure, updating the references in Google Search Console, Google Analytics and advertising platforms to ensure correct traffic tracking.
How to make an SEO-friendly migration from HTTP to HTTPS
One of the most common fears is that switching to HTTPS could negatively affect the site’s positioning, because a migration not carried out correctly can cause a loss of traffic.
The first essential step is to verify that all redirects are implemented without creating multiple chains, which slow down the loading of pages and can confuse search engines. Furthermore, it is essential to update the sitemap XML, indicating the new site structure through Search Console, and regenerate the file robots.txt to prevent some pages from being accidentally blocked in indexing.
During the process, constantly monitoring traffic will help identify any drops in visibility and promptly correct problems such as errors 404 resulting from invalid URLs.
Google’s official advice for the transition
In the video mentioned above, John Mueller from Google provided a practical checklist on the process of migrating from HTTP to HTTPS, divided into six steps that reduce the margin for error:
- Configure the HTTPS site.
- Verify ownership in Google Search Console.
- Test the HTTPS site extensively.
- Redirect all HTTP URLs to HTTPS URLs.
- Monitor the migration in Google Search Console.
- Configure HTTP Strict Transport Security (HSTS) – optional step.
So, first you need to set up the HTTPS site, possibly asking for support from your hosting service and acquiring the appropriate HTTPS certificate (in principle, any certificate supported by modern browsers such as Chrome is fine, even free ones).
The exact steps to follow here vary from website to website, Mueller explains: “Sometimes it’s just a matter of changing a setting, other times there’s a lot more to it.”
Secondly, you need to verify the site and ownership in Google Search Console, a crucial step in tracking down any problems associated with HTTPS version 2. You can also choose to verify the entire domain, to combine HTTP and HTTPS data in the same place, making sure to use the same settings. In particular, be careful to review the settings for removing geotargeting URLs, the settings for parameter URLs, the crawl rate settings and the disavow file, adding any co-owners in the Search Console.
The work continues with an important and in-depth phase of testing the site, also opening the test to some users: “Sometimes there are oddities that we have missed, and it is better to recognize and fix them before moving on to the HTTPS version,” explains Mueller.
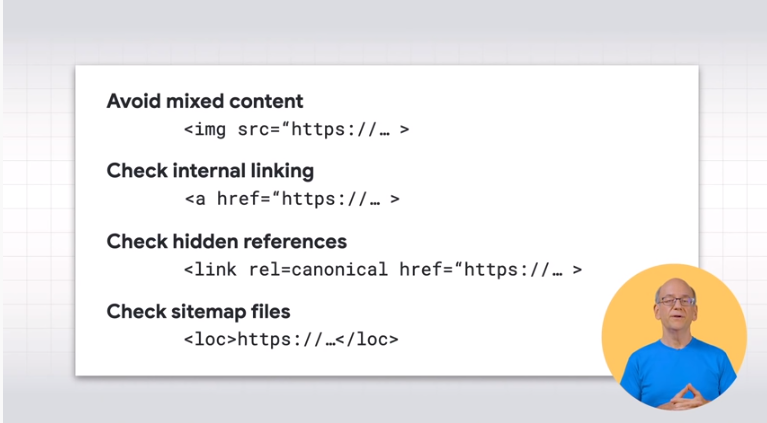
Among the aspects to be verified is first of all the possible presence of mixed content, i.e. when an HTTPS page includes HTTP elements, which can be, for example, embedded images, advertisements or analytics scripts. This is a negative aspect for security and browsers warn users when they recognize this problem.
We also need to check the internal links, to make sure that all the links on the website point to the HTTPS version: there are various tools to check this, but you can also just click on the browser bar and look at the URL that is displayed.
It is also important to analyze the hidden references – leading to HTTPS elements such as rel=canonical, rel=alternate, hreflang= link, as well as structured data – and check the sitemap files, which help Google to scan and index more efficiently.
The other steps in the process and enabling HSTS
Once the first three steps are completed, “the HTTPS site is ready, congratulations! Time to change everything,” jokes Mueller, who suggests using server-side redirects to forward all requests from the HTTP version to the new and correct HTTPS version.
It is advisable to double check all old URLs to verify that they redirect correctly, by manually doing random tests on each part of the website or by using an automatic tool for all URLs. If we have a sitemap, now is a good time to submit it, adds Google’s Search Relations Lead, because from now on search engines will start using our HTTPS URLs.
Then we move on to monitoring the migration in Search Console: it’s best to check Search Console regularly at the beginning, to identify any issues before they become problems. In particular, we need to check that the sitemap files are processed normally, that there are no unexpected crawl errors, that the index coverage report shows an increase for the HTTPS site and, last but not least, that users are finding the HTTPS site in Search.
The last step is optional and allows you to “move to the next level”: After making sure that everything is working as expected, and waiting a few months to fix the migration, it might be useful to consider enabling HSTS – HTTP Strict Transport Security – a system “to let browsers know that they no longer need to check the HTTP version of your site further”, because “it’s a long-term commitment on your part”.
Setting up HSTS is quite easy: just add a header to your server responses that tells browsers they no longer need to check the old HTTP version of your site’s URLs, even when a user tries to go there directly. In addition, there is one more step you can take, which is to add the site to the HSTS preload list, a shared list of sites that have committed to HTTPS used directly in Chrome: “A fairly big step, so it’s only recommended if you’re absolutely certain that everything is working properly on your HTTPS site”.
Post-migration checks and verification tools
After implementing HTTPS, you need to verify that all the site’s features are operational and that there are no resources still loaded via HTTP. The presence of mixed content can compromise security and generate warnings in browsers, reducing user confidence. The first check can be done directly from Google Chrome, by opening the developer console to identify calls to insecure resources. Tools such as Why No Padlock or SSL Labs Test provide details on any certificate configuration errors, while Google Search Console allows you to monitor the indexing of new HTTPS pages and report any crawling issues.
In addition to the initial scan, it is good practice to run periodic tests to ensure that the SSL certificate is always valid and that the security policies adopted remain compatible with the evolution of browsers and web standards.
HTTPS and the main critical issues to consider
In short, adopting HTTPS now seems to be a necessary choice to guarantee online security and reliability, but it can still present some technical problems that, if not managed correctly, compromise the functioning of the site and its visibility in search engines. The most frequent errors concern the management of SSL/TLS certificates, problems related to mixed content, and misconceptions that lead some sites not to implement the secure protocol.
Understanding the risks and adopting the best solutions helps to ensure a smooth transition, avoiding errors that could negatively affect the user experience and the positioning of the site. Ignoring these critical issues, on the other hand, could make the transition to HTTPS useless, leading to users receiving security warnings in their browsers, penalization in indexing or malfunctioning web pages.
Expired or incorrectly configured certificates
One of the most common errors is the use of SSL/TLS certificates that have expired, are incorrect or are not recognized by the main browsers. An invalid certificate leads to the display of security warnings that inform users of the risk of browsing an “unreliable” site, prompting them to abandon the session.
To avoid this problem, it is necessary to constantly monitor the status of the certificate, checking the expiry date and configuring an automatic renewal system, where possible. Let’s Encrypt, for example, provides free certificates valid for 90 days and automated update tools, reducing the risk of security being compromised by human error.
Another frequent problem concerns the use of self-signed certificates or certificates issued by unreliable authorities. A self-signed certificate is not recognized by browsers, making it useless for guaranteeing connection security. Websites must always rely on recognized certification authorities to avoid these warnings.
Configuration errors, such as enabling obsolete protocols or weak encryption algorithms, can also compromise the effectiveness of the certificate. To ensure compatibility with current standards, it is advisable to use only TLS 1.2 or TLS 1.3, avoiding previous versions such as TLS 1.0 and TLS 1.1, which are now deprecated for security reasons.
Mixed content errors
As we’ve already said, one of the most common technical problems on websites that migrate from HTTP to HTTPS is the presence of mixed content, i.e. pages served in HTTPS that load external resources that are still in HTTP. This phenomenon occurs when some elements of the page, such as images, style sheets or scripts, are called up using insecure URLs.
Modern browsers automatically block many of these elements, causing visible malfunctions on the pages. In some cases, instead of blocking the content, the browser reports the connection as “not completely secure”, compromising the perception of the site’s reliability in the eyes of the users.
To avoid this problem, it is essential to update all internal and external references to the site, verifying that each resource is loaded via and using special tools to identify any resources still served in HTTP. In some CMS platforms, such as WordPress, there are plugins that automate the URL conversion process to ensure full compatibility with the secure connection.
Adopting a correctly configured Content Security Policy (CSP) helps prevent future problems by automatically blocking the loading of unsafe resources and forcing the use of HTTPS on all page elements.
False myths about HTTPS
Despite being an essential requirement for any website, HTTPS is still surrounded by misconceptions that lead some site owners to delay its implementation.
One of the most widespread myths concerns the alleged slowness of HTTPS connections compared to HTTP. This belief was based on technical limitations that have long since been overcome. Today, thanks to the introduction of HTTP/2 and HTTP/3, sites served with HTTPS are faster than those in HTTP, thanks to improvements in request management and resource distribution.
Another common misconception is that HTTPS is only necessary for e-commerce sites or pages that handle sensitive data. In reality, Google and modern browsers penalize any HTTP site, regardless of the type of content hosted. This can reduce organic traffic, undermine user confidence and exclude access to advanced features such as Progressive Web Apps or push notifications, which are only available on secure connections.
Then there are those who believe that obtaining an SSL certificate is complicated or expensive, a statement that is now baseless. There are free solutions, such as Let’s Encrypt, which allow you to activate HTTPS in a few minutes through automated procedures. For those who require higher levels of validation, paid certificates guarantee additional benefits without prohibitive costs.
HTTPS: FAQs and questions to be answered
The adoption of HTTPS has transformed the way websites guarantee security, reliability and performance, becoming an essential requirement rather than a simple option. However, despite its widespread use, questions remain about how it works, its impact and implementation, especially for those considering the transition from HTTP.
Throughout this guide we have analyzed in detail the advantages of HTTPS, the SEO implications, the technical aspects and the critical issues to consider. Now, to complete the picture, we report some of the most common questions that emerge in user searches and specialized forums.
- What is HTTPS?
HTTPS (HyperText Transfer Protocol Secure) is a communication protocol that guarantees secure transmission of information between a browser and a website, using encryption to protect data from interception or modification during transfer.
- What does the acronym HTTPS mean?
The acronym stands for HyperText Transfer Protocol Secure and represents the encrypted version of the HTTP protocol, ensuring integrity, authentication and confidentiality in data transmission.
- Is HTTPS mandatory for all websites?
It is not a legal requirement in most cases, but it is strongly recommended for any site. Google and modern browsers flag HTTP sites as “not secure”, with negative impacts on user perception and potential repercussions on organic traffic and conversions. In addition, many advanced web features require an HTTPS connection to function properly.
- Does HTTPS really make a difference for SEO?
Google has confirmed several times that HTTPS is a ranking factor, even if its weight is lower compared to other aspects such as the quality of the content and the overall technical optimization of the site. However, in addition to the direct value in terms of positioning, it offers indirect advantages by improving the user experience, trust and compatibility with modern technologies, factors that influence the overall performance of the site.
- How do I get an HTTPS certificate?
SSL/TLS certificates can be obtained for free through services such as Let’s Encrypt or purchased from recognized certification authorities, such as DigiCert or GlobalSign, which offer higher levels of validation and greater reliability.
- Which HTTPS certificate should I use?
Any certificate supported by a modern web browser is fine: for example, Google recognizes and specifically recommends free certificates from the non-profit organization Let’s Encrypt.
- What is the difference between a free SSL certificate and a paid one?
Free certificates, such as those offered by Let’s Encrypt, guarantee effective encryption and are sufficient for most informational websites or blogs. Paid certificates offer higher levels of validation (OV, EV), useful for e-commerce companies or portals that need to demonstrate the organization’s identity to visitors, increasing user confidence.
- Does HTTPS slow down the loading of the site?
This was true in the early stages of adoption of the protocol, but today the combined use of HTTPS and HTTP/2 allows a site to load faster than with HTTP, thanks to techniques such as multiplexing and request compression.
- Does HTTPS guarantee that a site is secure?
HTTPS prevents data from being intercepted or modified, but it does not protect against all cyber threats. A malicious site can still obtain an HTTPS certificate and appear trustworthy to users. To ensure complete protection, additional security measures must be adopted, such as firewalls, protection against phishing and two-factor authentication.
- How can I verify if an HTTPS certificate is valid?
Browsers report any certification problems with explicit warnings. For a more thorough check, tools such as SSL Labs Test or Google Chrome DevTools allow you to check the validity, expiration and configuration of the certificate.
- If a site does not collect user data, does it still need HTTPS?
Yes. Any site that transmits data between the browser and a server can be vulnerable to interception or manipulation attacks. In addition, browsers warn users about HTTP sites, regardless of whether they contain login or payment forms.
- What is the difference between HTTP and HTTPS?
HTTP transmits data in plain text, making it vulnerable to interception by third parties. HTTPS uses TLS (Transport Layer Security) to encrypt information and ensure a secure connection. HTTPS sites are also marked as secure in browsers, while HTTP sites may be flagged as untrustworthy.
- Can switching from HTTP to HTTPS result in a loss of organic traffic?
If the migration is not handled correctly, yes. It is essential to implement global 301 redirects, update sitemaps and robots.txt files, and monitor indexing via Google Search Console to avoid problems with search engine visibility. A well-planned transition preserves traffic and can improve performance in the long term.
- How long does a migration take?
Google can usually process migrations within a week, if all the steps are correct. However, in practice the exact timing doesn’t really matter, as users will be redirected anyway.
- How long do you need to keep the redirects active?
Redirects should remain active forever: there is no reason not to redirect from HTTP to HTTPS after a migration.
- Is it possible to move just a few pages?
Technically it is possible to move just a few pages to HTTPS, such as the user login page, but in practice it doesn’t require much extra work to move the whole site, which is what should be done anyway.
- Is it possible to go back to HTTP after switching to HTTPS?
Technically yes, but it is strongly discouraged. Returning to HTTP would expose users to security risks, lose trust and possibly incur penalties in search engines.
- How can you check if a site uses HTTPS?
In the browser’s address bar, the site shows a closed padlock next to the URL. For a more detailed verification, you can use tools such as Google Chrome DevTools, SSL Labs Test, Why No Padlock or Analyze Mixed Content by SEOZoom.
- What does “mixed content” mean on an HTTPS site?
A page served over HTTPS that loads external resources (images, scripts, CSS) over HTTP will trigger a mixed content error. This behavior can compromise the security of the site and cause warnings in browsers. The solution is to update all resource links to use HTTPS.